Monday, December 28, 2020
Get Guarnateed DA50+ for %domain%
Get an amaazing Domain Authority score above 50 for your website and
increase sales and visibility in just 30 days
https://www.str8creative.co/product/moz-da-seo-plan/
Service is guaranteed
Regards
Mike
Str8 Creative
support@str8creative.co
Thursday, December 24, 2020
re: I need to make a website`s ranks go down
Yes, it is possible, with our service here
https://negativerseo.co/
for further information please email us here
support@negativerseo.co
thanks
Peter
Monday, December 14, 2020
Our most powerful SEO Ultimate Plan
Getting Top 10 Position in Search Engines is a Must for every Website if
you are really serious to do Online Business. If you are not in top 10 it
means you are getting only 5% of visitors for that particular keyword.
Please find more information on our plan here:
https://str8creative.co/product/seo-ultimate/
thanks
Mike
support@str8creative.co
Monday, December 7, 2020
re: Rank top 5 in the Google maps
Did you know that when someone is looking for a search term on their
phones, the Gmaps listings its what pop up first in the results?
Stop losing all that visibility and let us boost your G listing into the
tops for local terms
https://www.str8creative.co/product/1500-gmaps-citations/
thanks and regards
Mike
support@str8creative.co
Thursday, December 3, 2020
Buy quality business traffic for blogger.com
Do you want more quality visits engaging on your website?
Increase ranks and sales swith our business website traffic
Please find more information about our service here
https://basedbusinesstraffic.co/
thanks
Peter
Monday, November 30, 2020
Guaranteed Domain Authority 50/100
Here is how we can do it
https://www.str8creative.co/product/moz-da-seo-plan/
Regards
Mike
Str8 Creative
support@str8creative.co
Thursday, November 26, 2020
re: I need to make a website`s ranks go down
Yes, it is possible, with our service here
https://negativerseo.co/
for further information please email us here
support@negativerseo.co
thanks
Peter
Sunday, November 22, 2020
Cheap Monthly SEO plans %domain%
After checking your website SEO metrics and ranks, we determined that you
can get a real boost in ranks and visibility by using any of our plan below
https://www.cheapseosolutions.co/cheap-seo-packages/index.html
cheap and effective SEO plan
onpage SEO included
For the higher value plans, DA50 DR50 TF20 SEO metrics boost is inlcuded
thank you
Mike
support@cheapseosolutions.co
Sunday, October 25, 2020
re: re: Boost SEO with quality EDU backlinks
1000 Edu blog backlinks to improve your backlinks base and increase SEO
metrics and ranks
http://www.str8-creative.io/product/edu-backlinks/
Improve domain authority with more .edu blog backlinks
Unsubscribe from this newsletter
http://www.str8-creative.io/unsubscribe/
Tuesday, October 20, 2020
Domain Authority 50 for your website - Guaranteed Service
cent
for only 150 usd, you`ll have DA50 for your website, guaranteed
Order it today:
http://www.str8-creative.co/product/moz-da-seo-plan/
thanks
Alex Peters
Friday, October 9, 2020
re: I`m interested in your offer of Social Signals
17976889765154091533noreply
Glad to hear that, here are the details below
More information here:
http://www.realsocialsignals.co/buy-social-signals/
For the best ranking results, buy Monthly basis Social signals, provided
daily, month after month:
http://www.realsocialsignals.co/custom-social-signals/
Regards
Ibrahim
http://www.realsocialsignals.co/unsubscribe/
2018-11-9, tr, 19:37 17976889765154091533noreply
<17976889765154091533noreply@blogger.com> raše:
Hi there, Please send me the Social signals offer that we talked about over
the phone. I`m interested and I want to boost my SEO metrics with this new
SEO method^. Than!ks again, will wait your reply.
Sunday, October 4, 2020
re: Social traffic
proba-szyszki.htmlnoreply
here it is, social website traffic:
http://www.mgdots.co/detail.php?id=113
Full details attached
Regards
Amada Wiechmann �
Unsubscribe option is available on the footer of our website
Tuesday, September 29, 2020
Domain Authority 50 for your website - Guaranteed Service
cent
for only 150 usd, you`ll have DA50 for your website, guaranteed
Order it today:
http://www.str8-creative.co/product/moz-da-seo-plan/
thanks
Alex Peters
Tuesday, September 22, 2020
Stonne 1940 Big CoC Weekend Part 1
A small problem with running Big CoC games is that the scenarios are somewhat dependant on the number of players attending, and given the nature of the WHC the numbers can vary, Some players book months in advance, but often people will book relatively late so the scenario needed to be capable of being tweaked to fit this in. The nuts and bolts of the game don't alter that much, the idea being that each player will command an infantry (or armour) platoon, then the force as a whole has a degree of support which is then dished out. On the whole this is not a problem, but for quite a while we were looking at having six players (fine, 3 on 3) then suddenly the numbers went up to seven. My initial reaction was one of mild horror because it meant balancing the game for a three versus four. However, when I started looking at the way the Stonne game might play out, the imbalance of 3 platoons against 4 became more and more attractive.
 |
| A little Panhard 178. It bogged in the ditch...... |
They were encountering in these scenarios the 3e DIM (Division d'Infanterie Motorisée), supported by 3e DCr (Division Cuirassée)
Looking at the platoon lists for CoC the 1940 German infantry platoons are enormous. Each platoon contains 2 senior leaders and a 50mm mortar team plus 4 x 10 man sections, for a total of 44 men.
The French platoons are a similar size, with 2 platoon leaders (1 senior, 1 junior) a VB rifle grenade team of a junior leader with 4 men. plus 3 sections of 11 for a total of 40 men.
So if we had seven players, with 3 on the German side and 4 for the French it wouldn't be too bad. 1 player a side would be playing a tank platoon anyway, so it would be 2 German infantry platoons against 3 French, however that is actually 8 German sections opposed to 9 French, making it less unbalanced than first appears. A little extra tweaking by making the Germans "superior regulars" meaning they treat rolls on their command dice of a single six also as a 5, giving them more CoC dice pips during the game, plus increasing the size of their panzer II platoon to a whopping 5 vehicles would compensate for the additional French numbers. Additionally, each German platoon would start with a full Chain of Command Dice.
Given the nature of the fighting in Stonne (the village apparently changed hands 17 times in 3 days), it lent itself to a relatively straightforward narrative: i.e. Attack and counterattack- So I decided to make the first game an attack/defence scenario with the Germans on the offensive at the eastern end of the table, the second game was to be another attack/defence with the French on the offensive at the western end of the table. Game 3 was to be in the central area of the table with the Germans attacking in an "attack on an objective" scenario.
I planned a 4th scenario which was to be played out on new terrain to the east of Stonne and that would have been the French conducting a flank attack. However, time sadly ran out. I'm sure we will do it one day.
French section enters central Stonne
Monday, September 21, 2020
Addicted!
Today was spent the same as usual lately by loading up the truck so I can get some more stuff moved to our new place.
All day I couldn't stay away from the Zombies in my pocket app and played 15+ games of it today losing most and winning few but having a blast playing
I seem to be heavily addicted to the game in my free time like I used to be long ago, lol.
As always, thank you for reading and don't forget to stop and smell the meeples! :)
-Tim
Friday, September 18, 2020
1500 google maps citations cheap
http://www.str8-creative.io/product/1500-gmaps-citations/
regards,
Str8 Creative
Saturday, September 12, 2020
People Behind The Meeples - Episode 241: Hameed Moore

Welcome to People Behind the Meeples, a series of interviews with indie game designers. Here you'll find out more than you ever wanted to know about the people who make the best games that you may or may not have heard of before. If you'd like to be featured, head over to http://gjjgames.blogspot.com/p/game-designer-interview-questionnaire.html and fill out the questionnaire! You can find all the interviews here: People Behind the Meeples. Support me on Patreon!
| Name: | Hameed Moore |
|---|---|
| Email: | mooregames19@gmail.com |
| Location: | Norway |
| Day Job: | Student |
| Designing: | Two to five years. |
| Facebook: | Moore Games LLC |
| Twitter: | @MooreGamesLLC |
| Instagram: | @MooreGamesLLC |
| Other: | UnPub 9 |
Hameed Moore
Interviewed on: 7/16/2020
This week's interview is with Hameed Moore, a designer working on his first game that will be making its way to Kickstarter this October. So keep your eye out for Vendarla, and read on to learn more about Hameed and his other projects.
Some Basics
Tell me a bit about yourself.
How long have you been designing tabletop games?
Two to five years.
Why did you start designing tabletop games?
From new Lego designs to fantasy RPGs, I've always had a passion for designing stuff ever since I was kid. I really enjoy history and fantasy subjects and tabletop design gives me that platform to bring those subjects to life in a format of a game.
What game or games are you currently working on?
Press your luck (Vendarla), Worker placement, Co-op deck builder
Have you designed any games that have been published?
Not yet
What is your day job?
Student
Your Gaming Tastes
My readers would like to know more about you as a gamer.
Where do you prefer to play games?
In a house
Who do you normally game with?
Wife, family, and friends
If you were to invite a few friends together for game night tonight, what games would you play?
If we have 7 people then 7 Wonders always! Less than 7, Orleans, Valeria Card/Villages, Mansions of Madness, Dice Forge, Terraforming Mars
And what snacks would you eat?
Chips and nuts
Do you like to have music playing while you play games? If so, what kind?
It depends on the theme of the game. If I was playing a civilization themed game then I would play music from a civilization soundtrack.
What's your favorite FLGS?
Games Unlimited in Pittsburgh, PA and Outland in Bergen Norway
What is your current favorite game? Least favorite that you still enjoy? Worst game you ever played?
My favorite is 7 Wonders, Least favorite but still enjoy Dwarven Smithy, and worst game is Quests of Valeria
What is your favorite game mechanic? How about your least favorite?
Favorite is worker placement. Least is trick taking
What's your favorite game that you just can't ever seem to get to the table?
I don't have that problem but if I have to pick one it would be Through the Ages.
What styles of games do you play?
I like to play Board Games, Card Games, Miniatures Games, RPG Games, Video Games
Do you design different styles of games than what you play?
I like to design Board Games, Card Games
OK, here's a pretty polarizing game. Do you like and play Cards Against Humanity?
Yes
You as a Designer
OK, now the bit that sets you apart from the typical gamer. Let's find out about you as a game designer.
When you design games, do you come up with a theme first and build the mechanics around that? Or do you come up with mechanics and then add a theme? Or something else?
Mechanics first then the theme.
Have you ever entered or won a game design competition?
No
Do you have a current favorite game designer or idol?
No
Where or when or how do you get your inspiration or come up with your best ideas?
From ancient history and fantasy works
How do you go about playtesting your games?
I set up private game nights for a selected group. Eventually I will take my prototype to any board game meetup events to find new testers.
Do you like to work alone or as part of a team? Co-designers, artists, etc.?
With a team, my wife is a UX designer so she helps me with some ideas and all of the design layout.
What do you feel is your biggest challenge as a game designer?
Marketing your game.
If you could design a game within any IP, what would it be?
I would like to design a board game similar to World of Warcraft.
What do you wish someone had told you a long time ago about designing games?
How to market your games through social media and other platforms.
What advice would you like to share about designing games?
Have fun and be open-minded to people's comments about your game.
Would you like to tell my readers what games you're working on and how far along they are?
I'm planning to crowdfund: Vendarla - a competitive press your luck resource management game.
Games I feel are in the final development and tweaking stage are: Vendarla
Games that I'm playtesting are: Worker placement city building game
Games that are in the early stages of development and beta testing are: Co-op deck builder adventure game
And games that are still in the very early idea phase are: Civilization style game
Are you a member of any Facebook or other design groups? (Game Maker's Lab, Card and Board Game Developers Guild, etc.)
Yes, Board Game Reviewers & Media, BG Design Lab Community, BG Geek Crowdfunding Group, BG Revolution Community, BGG
And the oddly personal, but harmless stuff…
OK, enough of the game stuff, let's find out what really makes you tick! These are the questions that I'm sure are on everyone's minds!
Star Trek or Star Wars? Coke or Pepsi? VHS or Betamax?
Star Wars, Coke-zero, VHS
What hobbies do you have besides tabletop games?
Reading, PC gaming, traveling, and hiking
What is something you learned in the last week?
Getting people to subscribe to a newsletter early on in the process is really important.
Favorite type of music? Books? Movies?
Favorite type of music - Classical Favorite type of books - Ancient history, medieval history, science-fiction/fantasy Favorite type of Movies - Historical, action, comedies, science-fiction/fantasy, romantic comedies
What was the last book you read?
Lords of the North by Bernard Cornwell
Do you play any musical instruments?
No
Tell us something about yourself that you think might surprise people.
I can be shy at first
Tell us about something crazy that you once did.
Attended a random person's graduation party with some friends.
Biggest accident that turned out awesome?
Can't think of anything
Who is your idol?
Roman Emperor Aurelian
What would you do if you had a time machine?
Visit the Roman Empire during its Pax Romana
Are you an extrovert or introvert?
Introvert until I get to know the people
If you could be any superhero, which one would you be?
Silver Surfer
Have any pets?
No
When the next asteroid hits Earth, causing the Yellowstone caldera to explode, California to fall into the ocean, the sea levels to rise, and the next ice age to set in, what current games or other pastimes do you think (or hope) will survive into the next era of human civilization? What do you hope is underneath that asteroid to be wiped out of the human consciousness forever?
I hope we can find a way to stop the next asteroid from hitting Earth. Board games will survive because we have been playing board games since the times of the ancient Egyptians and Sumerians.
Just a Bit More
Thanks for answering all my crazy questions! Is there anything else you'd like to tell my readers?
Game on!! I plan on launching the Kickstarter campaign for Vendarla in October 2020.
Thank you for reading this People Behind the Meeples indie game designer interview! You can find all the interviews here: People Behind the Meeples and if you'd like to be featured yourself, you can fill out the questionnaire here: http://gjjgames.blogspot.com/p/game-designer-interview-questionnaire.html
Did you like this interview? Please show your support: Support me on Patreon! Or click the heart at Board Game Links
 , like GJJ Games on Facebook
, like GJJ Games on Facebook  , or follow on Twitter
, or follow on Twitter  . And be sure to check out my games on Tabletop Generation.
. And be sure to check out my games on Tabletop Generation.Game 378: Goodcode's Cavern (1982) And Romero/Carmack Corrections
Gebelli Software (publisher)
 |
| Stepping into the first room. |
 |
| This room is pink with a thick carpet and there's moaning. |
 |
| Hot tacos indeed. Although I suspect if I saw a blue grizzly bear, I'd start blaming something else I got in Mexico. |
 |
| Finding a "nickel headband" and then checking my status. |
 |
| The mammoth russet vampire was a little too much for me, so I zapped him with the wand. I'm glad I did, because the colossal gold knife was worth a lot of money. |
 |
| A demon convinces me to pay reparations. |
 |
| No, but you can resurrect me. |
 |
| Room 80 on Level 1. |
 |
| The winning screens. |
 |
| I have no idea what's happening here. |
1991 was a major transition year for Carmack and his new partner, John Romero. At the age of 20, Carmack had gotten a job two years prior at Softdisk, largely on the strength of his Dark Designs series. But he and the other developers grew to despise the sweatshop-like atmosphere of Softdisk and the monthly programming demands. He and Romero began moonlighting by selling their own games--principally the Commander Keen series--as shareware on bulletin board services. When Softdisk found out about these games, and that the pair had been using the company's computers to write them, both threats of a lawsuit and offers of a contract followed. The messy result was that Carmack and Romero left the company but agreed to continue to produce one game every 2 months for Softdisk's magazines. Thus, a couple years later, after the team had changed the gaming world forever with Wolfenstein 3D and DOOM, you see them credited on the occasional diskmag title like Cyberchess and Dangerous Dave Goes Nutz!
- I was a year late; 1990 was the year most of this happened. Romero worked at Softdisk prior to Carmack and was actually the one who hired Carmack, not because of Dark Designs but because of a tennis game plus his obvious facility with programming.
- Romero and Carmack loved working at Softdisk and only left because it was the wrong sort of publisher to take advantage of the horizontal scrolling technology that the duo would use in Wolfenstein 3D and DOOM.
- It was actually the president of Softdisk, Al Vekovius, who suggested that Carmack, Romero, and Tom Hall start their own company. There were no lawsuits and no threats; Carmack and Romero kept working for Softdisk for a year to avoid leaving the company in a lurch.
- The reason Carmack and Romero are credited on so many Softdisk titles stretching into the mid-1990s is that those titles used technology and code that Carmack and Romero had created. They otherwise had no involvement in games like Cyberchess and Dangerous Dave Goes Nutz!
Friday, September 4, 2020
D-E-D Dead!
Today for the #2019gameaday challenge I played a game of Colt Express on the mobile app. It was a great game but I'm a little biased about the game, lol!
I didn't end up winning but I felt a bit rusty with the game. I can't wait to play it again and trying to win!
As always, thank you for reading and don't forget to stop and smell the meeples! :)
-Tim
Sunday, August 30, 2020
Router-Exploit-Shovel: An Automated Application Generator For Stack Overflow Types On Wireless Routers
Router-Exploit-Shovel is an automated application generation for Stack Overflow types on Wireless Routers.
Router exploits shovel is an automated application generation tool for stack overflow types on wireless routers. The tool implements the key functions of exploits, it can adapt to the length of the data padding on the stack, generate the ROP chain, generate the encoded shellcode, and finally assemble them into a complete attack code. The user only needs to attach the attack code to the overflow location of the POC to complete the Exploit of the remote code execution.
The tool supports MIPSel and MIPSeb.Run on Ubuntu 16.04 64bit.
Router-Exploit-Shovel's Installation
Open your Terminal and enter these commands:
Usage
Example:
python3 Router_Exploit_Shovel.py -b test_binaries/mipseb-httpd -l test_binaries/libuClibc-0.9.30.so -o 0x00478584Router-Exploit-Shovel's screenshot
Code structure
ROP chain generation
This tool uses pattern to generate ROP chains. Extract patterns from common ROP exploitation procedure. Use regex matching to find available gadgets to fill up chain strings. Base64 encoding is to avoid duplicate character escapes. For example:
Attackblocks
You can get attackblocks generated in results/attackBlocks.txt. Such as:
You might like these similar tools:
- eXpliot - Internet Of Things Exploitation Framework
- RouterSploit: Exploitation Framework for Embedded Devices
More information
- Pentest Tools For Android
- Hacking Tools For Pc
- Hacking Tools Kit
- Pentest Tools Download
- Best Hacking Tools 2019
- Hacking Tools Software
- Underground Hacker Sites
- Pentest Tools Nmap
- Hacking Tools For Windows Free Download
- Hack Tools
- Hacker Search Tools
- Hacker Techniques Tools And Incident Handling
- Hacker Tools For Ios
- Pentest Automation Tools
- How To Hack
- How To Make Hacking Tools
- Hack Website Online Tool
- Pentest Tools Website Vulnerability
- Hacking Tools Free Download
- Nsa Hack Tools
- Hacker Tools
- Hack Rom Tools
- Hack Tools
- Tools 4 Hack
- Best Pentesting Tools 2018
- Hacking Tools Online
- Hacker Tools Online
- How To Install Pentest Tools In Ubuntu
- Pentest Tools Free
- Hacking Tools For Beginners
- Wifi Hacker Tools For Windows
- Hacking Tools Github
- Hacker Security Tools
- Hacker Security Tools
- Hacker Tools Hardware
- Hacking Tools Online
- Hacker Tools For Ios
- Hack Tool Apk No Root
- Hacking Tools Pc
- Hack And Tools
- Hacking Tools Windows
- Hak5 Tools
- Hacker Tools Linux
- Pentest Tools Free
- Hacker Tools
- Hacker Tools For Windows
- Hacker Tools Software
- What Is Hacking Tools
- Hacking Tools Download
- Pentest Tools Free
- New Hacker Tools
- Hacker Tools For Mac
- Hacker Tools 2020
- Pentest Tools Download
- Hack Tools
- How To Make Hacking Tools
- Hack Tools Pc
- Hacker Hardware Tools
- Pentest Tools Windows
- Hack And Tools
- Hacker Tools 2020
12 Ways To Hack Facebook Account Passwords And Its Proeven Tion Techques 2020
Being a FB white hat hacker, I get following questions frequently from people:
- Can you refer any reliable Facebook hacker? (After me denying their hacking request 😛 )
- Is there any online FB cracker tool?
- Where can I get FB hacking software?
- Is there any free password finder?
- How can I hack someone's Facebook account easily?
To the best of my knowledge, there is no hacking tool. You won't be able to find it anywhere. However, you will find many websites claiming that they are providing free hack tool (either online or offline), but you cannot download the password file without completing a survey. Even after going through a tiresome process of completing a survey, you would have got nothing in the end. These things are posted only with the intention of making money. Don't waste your precious time in searching such hack tool.
If you want to know how hackers can hack someone's FB account, please go ahead and read the techniques listed below. The most successful method among all of these techniques is phishing. Phishing enables someone with no or little technical knowledge to hack account's password easily in just a few minutes.
Some of the techniques listed below are not applicable only to FB but also to all daily used internet websites, such as Google, Twitter, Yahoo etc.
You won't be vulnerable to hacking if you understand how hacking works
This article is written with the aim of educating people about how hacking works and how should they prevent it. Please don't use these techniques for malicious purposes.
1 Phishing
Phishing is the most common technique used for hacking FB passwords. It is very easy for someone who is having little technical knowledge to get a phishing page done. That is why phishing is so popular. Many people have become a victim of Phishing page due to its trustworthy layout and appearance.
How does phishing work?
In simple words, phishing is a process of creating a duplicate copy of the reputed website's page with the intention of stealing user's password, or other sensitive information like credit card details. In our topic, it means creating a page which perfectly looks like FB login page but in a different URL like fakebook.com, or faecbook.com, or any URL that pretends to be legit. When a user lands on such a page, he/she may think that is the real Facebook login page, asking him/her to provide his/her username and password. So, the people who do not find phishing page suspicious are going to enter their username & password. The password information will be sent to the hacker who created the phishing page. At the same time, the victim gets redirected to original FB page.
Example: John is a programmer. He creates an FB login page with some scripts that enable him to get the username and password information. John puts this fake login page in https://www.facebouk.com/make-money-online-tricks. Peter is a friend of John. John sends a message to Peter, "Hey Peter, I have found a free trick to make money online, you should definitely take a look at https://www.facebouk.com/make-money-online-tricks-free". Peter navigates to the link and see a FB login page. As usual, Peter enters his username and password on it.
The hacking part
The username and password of Peter is sent to John and Peter is redirected to a money making tips page https://www.facebouk.com/make-money-online-tricks-tips-free.html. That's all; Peter's Facebook account is hacked.
Please note that phishing is done by a third person through emails; that is how it happens most of the time. So always beware of phishing emails, else you may lose your Facebook account, or credit card details, or any other sensitive data. Learn more about phishing.
How can you protect yourself against online FB phishing?
Hackers can reach you in many ways; email, personal messages, FB messages, website ads etc. Clicking any links from these messages will lead you to a FB login page. Whenever you find an FB login page, you should note only one thing which is URL. Because nobody can spoof/use Facebook URL except when there are some XSS zero-day vulnerabilities, but that's very rare.
- What is the URL you see in browser address bar?
- Is that really https://www.facebook.com/ (Trailing slash is very important since it is the only separator in Google chrome to distinguish domain and subdomain. Check out the below examples to know the difference)?
- Is there a green color secure symbol (HTTPS) provided in the address bar?
Bearing these questions in mind should prevent you from the hacking of online phishing pages. Also, see the below examples of phishing pages.
Some super perfect phishing pages
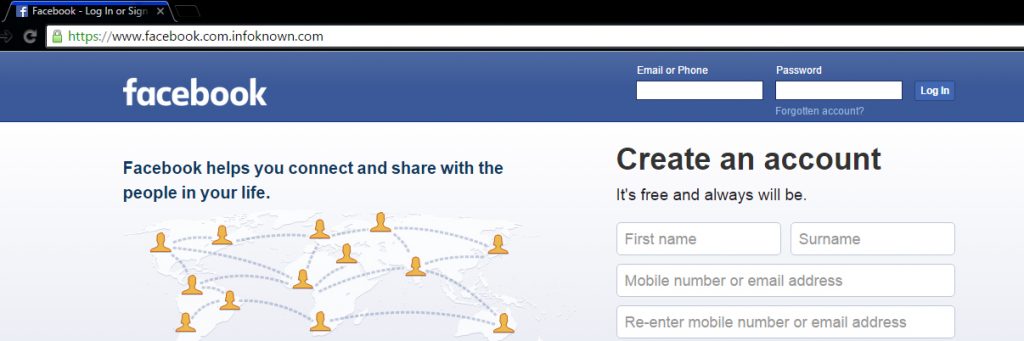
Most of the people won't suspect this page (snapshot given above) since there is an https prefix with a green color secure icon and also there is no mistake in www.facebook.com. But, this is a phishing page. How? Note the URL correctly. It is https://www.facebook.com.infoknown.com. So, www.facebook.com is a sub-domain of infoknown.com. Google Chrome does not differentiate the sub-domain and domain, unlike Firefox does.
One can obtain SSL Certificates (HTTPS) from many online vendors. A few vendors give SSL Certificate for Free for 1 year. It is not a big deal for a novice to create a perfect phishing page like the one given above. So, beware of it.
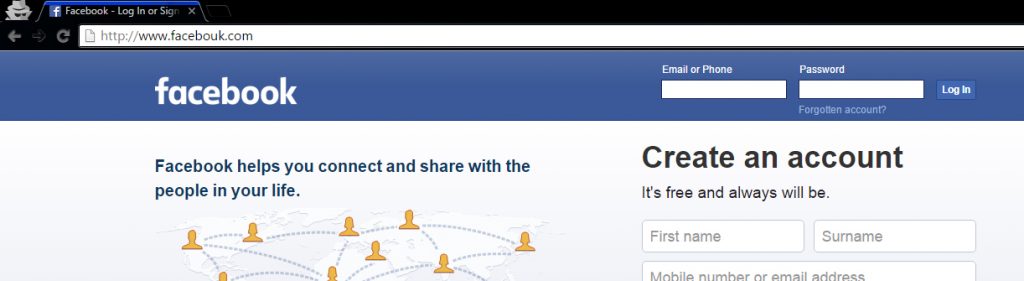
This is a normal FB Phishing page with some modification in the word Facebook.
2 Social Engineering
This is the second most common technique for hacking Facebook accounts. In fact, this method shouldn't come under Hacking, since much knowledge is not required for this method. I am listing this method under hacking to ensure the list of most common techniques used for FB account hacking in their respective order. Social engineering is basically a process of gathering information about someone, whose account you need to hack. The information may be his/her date of birth, mobile number, boyfriend/girlfriend's mobile number, nickname, mother's name, native place etc.
How does Social Engineering work?
Security Question
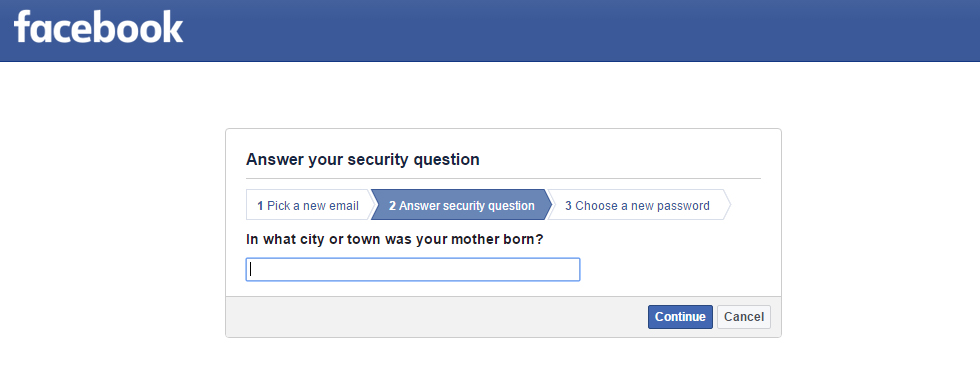
Many websites have a common password reset option called Security Question. Most common security questions are :
What is your nickname?
Who is your first-grade teacher?
What is your native place?
or
Any custom questions defined by the user.
Obtaining such information from the respective people may let us hack into their account. So, if anyone comes to know the answer to it, they will be able to hack your account using forgot password option.
Most Common and Weak Passwords
Security Question does not let you get into others FB account easily. But, setting a weak password could easily allow any of your friends to hack your account.
What is a weak password?
A password that is easily guessable by a third person is known as a weak password.
Most common passwords
- Mobile Number
- Nickname / Name and Date of Birth Conjunction
- Boy Friend's Mobile Number / Girl Friend's Mobile Number – Most of the lovers 😛
- Girl Friend's / Boy Friend's Name – Most of the lovers 😛
- Boy or Girl Friend Name Combination
- Bike Number
- Unused / Old Mobile Number
- Pet Name
- Closest Person Name (can be friends too)
Now, be honest and comment here if you are one of the people who have any one of the common passwords mentioned above. Please don't forget to change your password before making a comment 😉
How can you protect yourself from Social Engineering?
Security Question
Don't have a weak or familiar security question/answer. Therefore, it should be known only to you. You can set your security question here. Fortunately, Facebook has a lockout period of 24 hours before giving access to the one who successfully answered the security question, meaning that the hacker cannot enter into your account until 24 hours. So you can prevent the hacking attempt by logging in to your account in the 24 hours lockout period.
Additionally, FB provides an option called "Login Alerts" under Facebook Security Settings. You should add your mobile or email there to get notified whenever your account is logged in to a new or unknown device.
Most Common and Weak Passwords
It is very simple. Change your password now if you have any one of the weak passwords stated above.
You might also be interested in hacking facebook fan page article
3 Plain Password Grabbing

This is another common method used to steal Facebook user's password. Most people are unaware of this method, but traditional hackers use this method to hack user accounts.
How does Plain Password Grabbing works?
In this method, the Facebook hacker targets a particularly low-quality website, where the victim is a member and hacks their database to get the stored plain username & password of victim.
How could the hacker/attacker get access to Facebook?
Many of us use the same password for FB and also for some poor xyz.com. So, it is easy for a hacker to get your password through the low-quality poorxyz.com.
In another scenario, the hacker/attacker creates a website with the intention of getting victim's password, so when the victim registers his/her account using email and creates a password, those details will get stored in the database of the hacker/attacker. Thus hacker gets access to victim's account.
Common people, who use same email and password for these kinds of low-quality websites, may end up losing their Facebook account.
How can you protect yourself from Facebook Plain Password Grabbing?
You should never trust the third party low-quality websites. Even passwords of popular websites, like LinkedIn, are insecure and vulnerable to hacking. So, never and ever trust the third party low-quality websites.
Most of the website developers are storing plain passwords in their database without even thinking about encryption or security. This makes Facebook hackers' job easy since the password is in plain text format.
Best way to prevent this method is to have a unique password at least for websites that you really trust. Don't use your FB password for any other website/portal, so your password will be safe .
4 Key Logger

A keylogger is a software tool used to record keystrokes on a computer or mobile device. This, in turn, records everything you type using your keyboard and store it for use. Generally, keyloggers are installed as application software in operating systems to track keystrokes, but there are hardware keyloggers as well.
Hardware keyloggers also are known as physical keyloggers attached to a computer in a USB port records everything before it sends the keyboard data to the computer. There are various mobile keyloggers, that perform the same action on various operating systems.
How Key Logging works?
All keyloggers run in the background (except trial versions) and won't be viewable to users until you know the keylogger password and shortcut used to view it. It will record all the keys pressed and give you a detailed report of when and what keys are used for what application – Simply, a clean report to identify passwords.
Anyone who is reading the keylogger logs is able to see the Facebook password or any passwords and sensitive information typed, like credit cards, bank username, password etc. Whenever you log in to a public computer, there are chances to lose your Facebook password to someone else.
Hardware keyloggers are identifiable in case of your personal computer but are hard in case of public computers.
In another scenario, your friend/colleague/neighbor could ask you to log in using their computer as a help. If their intention is to get your password, then you are most likely to lose your Facebook account to the hacker.
Nowadays, many people are using mobile keyloggers. It enables to track the keypad of mobile. So, any sensitive information typed on the mobile keypad is vulnerable to hacking.
How can you protect yourself from Key Logging?
You need not be afraid of keyloggers when you use your personal computer since you are the only one who is going to access it. But, whenever you use any public computer or your friend's computer, you should not trust it.
I always suggest my friends use On-Screen Keyboard whenever they are in need to type a password. Also, please make sure that nobody is checking your screen when you type your password because your screen would expose what you had typed. In windows, there is an inbuilt tool called On-Screen Keyboard that helps us to select keys using the mouse.
You can open OSK by using the Run dialog box. Winkey + R to open Run dialog box, type OSK and then press Enter. Nowadays, many banking portals provide a screen keyboard in the browser itself. So, please make use of it whenever you are surfing on public computers. On-Screen Keyboard helps even when hardware keyloggers are installed.
Never use third-party mobile keypad apps unless you really trust the publisher because the app may track all of your keystrokes and send it to the publisher.
5 Browser Extension Hacker
This method doesn't let the Facebook hacker/attacker gain complete access to your Facebook account, however, gives some power to control your account indirectly. I've seen multiple Google Chrome and Firefox add-ons, which secretly perform actions, like following a person, like a page on behalf of your Facebook profile, etc.
How Browser extension hack works?
When you visit some malicious websites or web pages, you will be prompted to install a browser add-on. Once you install the add-on, it will perform all the tasks described by the hacker or attacker who created it. Some primary actions are posting status updates on your wall, liking an FB page, following a person, adding you to some Facebook groups, inviting your friends to like a page, or join a Facebook group etc. You may not know these things happening on your FB account until you check your Facebook activity log periodically.
How can you prevent browser extension Facebook hack?
You should monitor your activities using Activity Log. You must not trust any third party websites prompting you to add a browser extension. Install add-on only from the browser store, that too only from trusted publishers. Why should you risk your account if you don't know the publisher or intention of the add-on? Therefore, always stay away from these malicious browser extensions.
6 Malicious Application Hack
Always remember that all the apps you use on Facebook are owned by third-party publishers and not by Facebook. Of course, there are a few exceptions like Instagram. A malicious application, which is requesting your permission, will do almost all kind of spam stuff on your Facebook profile.
How malicious application hack works?
Whenever you find Login using the Facebook option on any website, you should come to know that it is a third party Facebook application not owned by Facebook. When you click Login using Facebook, you will be shown a permission dialog box with the requested permission details. Once you click okay button, the requested personal details can be accessed from FB or the requested actions can be performed in your FB account on your behalf.
What could a third party application do on your Facebook account?
- Post photos and status update
- Share link to your timeline or to any group you belong
- Manage your page
- Post on behalf of you on the Facebook pages you own
- Access your personal information
- Access your photos including "Only me" privacy photos; sometimes they can further access your mobile photos using a Facebook vulnerability like the one I found (Don't worry, it's completely fixed now 😉 ).
These are just examples of what can be done. What if the application you are using is malicious? It could spam your Facebook account with a bunch of worthless contents.
How can you prevent yourself from malicious application hack?
You should always beware of what permissions you give to a Facebook application even though FB is reviewing application's permission requests. Don't give permission to an application if you don't trust the website or application.
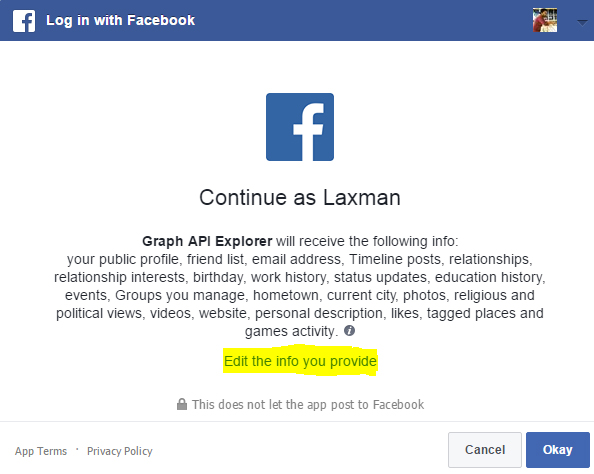
You can edit the information that you give to an application in the permission dialog box (snapshot given above). Also, you should review the applications that have access to your Facebook account here if you think you had given access to malicious applications.
7 Facebook Account Hacker Software
You might have seen or downloaded many Facebook account hacker software, but none of them could truly hack Facebook password. Hacking your Facebook password instead of the target user is what it actually does.
How does Facebook account hacker software work?
People who try to hack Facebook account usually download software that is available on various websites. The software will collect the victim's password (the one who downloaded this software) as soon as it is opened or installed. Some software prompt you to enter Facebook username and password. They will store your password in their database collection of passwords. Few other software gain administrative privilege from you to install background keylogger to get your keystrokes including the Facebook password.
How can you prevent yourself from Facebook hacking software?
Don't trust Facebook hacking software. There is no real hacking software available on the Internet as I had said earlier.
8 Malicious Mobile Application
There are a lot of mobile applications that secretly steal Facebook access token from your mobile device. Facebook mobile app functions through API, where access-token stored in your mobile's internal memory is used for authentication. It is more like your username and password. So, if someone steals your access-token, then he/she is likely to have full access to your Facebook account.
How malicious mobile application software works?
Facebook Application Interface do not require username or password every time to get user data. It just needs secret access-token to retrieve user's data. Facebook mobile app stores the access token in mobile's memory. The app's part of the memory is accessible only to the respective application. Mobile apps that have administrative privilege can access other app's data. For example, gaining admin privilege in a rooted android phone could allow an application to steal your access token. A hacker can do a lot of malicious things if he/she gets your access token.
How can you prevent yourself from malicious mobile applications?
- Install mobile apps only from trusted publishers.
- Don't root your mobile device.
- Logout Facebook from your mobile device frequently to get your access token expired.
- Change your Facebook password frequently.
9 Browser Vulnerabilities

Browser Vulnerabilities are security bugs, which exist in older versions of mobile and desktop browsers.
How does browser vulnerabilities work on Facebook hacking?
Most browser vulnerabilities are exploited through an older version of the browser since all the zero days are patched by browser vendor once it is reported by researchers around the world. For example, Browser Same Origin Policy Vulnerability could allow a hacker/attacker to read the response of any Page like facebook.com and could be able to perform any action on your Facebook account since they are able to read the response by accessing the Facebook origin. Android Chrome SOP bypass by Rafay Baloch is one such vulnerability that is affecting Android web-view in Android < 4.4.
How can you prevent yourself from browser vulnerabilities?
You should always update your browser and operating system once there is an update available. Keeping an older version always has many risk factors involved.
Self XSS is also known as Self Cross Site Scripting. XSS is basically a web security vulnerability, which enables hackers to inject scripts into web pages used by other users. What is self XSS then? Self XSS is a kind of social engineering attack, where a victim accidentally executes a script, thus exploiting it to the hacker.
How does self XSS scam work?
In this method, hacker promises to help you hack somebody else's FB account. Instead of giving you access to someone else's account, the hacker tricks you into running malicious Javascript in your browser console that gives a hacker the ability to manipulate your account. Facebook hackers use this technique to add you in groups, add your friends to the group, post on your wall, add your friends in comments etc.
How can you prevent yourself from self XSS?
Self XSS is something that you let hackers to hack your account. So never and ever copy & paste the code given by someone in your browser, otherwise, you will get your Facebook account hacked.
11 Trojan Horses
Trojan Horse is a malicious program, which is used to spy and control a computer by misleading users of its true intent. Malware Trojan can also be called as Remote Key Logger since it records keystrokes of all the applications of our computer and sends it to the hacker online.
How do Trojan Horses work?
A software you think legit might be a trojan. A PDF you don't suspect might contain a trojan. An AVI media file given by someone might be a trojan. The Trojan horse runs in the background process, collects information and send it to the hacker. Trojan Horse can be sent in any form through any medium, like pen drive, iPod, website, or email. In our topic, Trojan records FB password that you have typed in your browser and sends it to the Facebook hacker using the Internet.
How can you prevent yourself from Trojan?
- Do not
- install programs from unknown online sources
- play media files received from an unknown source
- open any kind of files downloaded from untrusted sources
- insert pen drive from any suspicious people.
- Do have an updated anti-virus software installed on your computer.
Keeping your anti-virus software up to date does not guarantee you to stay safe from hacking. Basically, an anti-virus software is a collection of detected malware and viruses. Its job is to compare each and every file with the database of viruses. There are many numbers of software, which enable us to create undetectable Trojans. But, it is very unlikely to target a common man with undetectable Trojanware. So, keeping an antivirus program up to date is protective to large extent. Don't forget to update your anti-virus software once an update is available.
12 FB Zero Day
Zero Day is a security vulnerability that is unknown to the respective software vendor. In our context, undiscovered Facebook vulnerabilities are called FB Zero Day.
How does Zero Day hacking work?
FB Zero Day vulnerabilities are very rare since Facebook has a bug bounty program, where security researchers around the world participate and report zero-day vulnerabilities. Zero-day is basically a security loophole that is unknown to the software vendor.
There are two types of people who find Zero Day vulnerabilities. The first case is Security Researchers and Bug hunters, who make a responsible disclosure about the vulnerability to the software vendor; FB in our context. Another case falls on the evil side. Blackhat hackers who find Zero Day vulnerabilities don't disclose it to Facebook and they will use it for their personal benefit of hacking.
@EVERYTHING NT
More information
- Hack Tools
- Hak5 Tools
- World No 1 Hacker Software
- Hacking Tools Hardware
- Hack Rom Tools
- Hack App
- Termux Hacking Tools 2019
- Hak5 Tools
- Physical Pentest Tools
- Hacking Tools 2020
- Hacker Tools For Pc
- Game Hacking
- Hacking Tools Mac
- New Hacker Tools
- New Hack Tools
- Hacking Tools For Pc
- Hacker Tools Github
- How To Install Pentest Tools In Ubuntu
- Pentest Tools Kali Linux
- Hacking Tools 2020
- Hack Apps
- Pentest Tools Port Scanner
- Hackrf Tools
- Black Hat Hacker Tools
- Pentest Automation Tools
- Pentest Tools Download
- Hacker Search Tools
- Hack Tools Mac
- Pentest Recon Tools
- Hacker Tools List
- Pentest Tools Online
- Hacking App
- Pentest Tools Bluekeep
- Hacking Tools For Windows 7
- Pentest Tools Android
- What Are Hacking Tools
- Hacking Tools Mac
- Hack Tools
- Hacking Tools Download
- Hacking Tools Hardware
- Hack Tools
- Black Hat Hacker Tools
- Pentest Tools Android
- Hacker
- Tools 4 Hack
- Hack Tool Apk
- Pentest Tools Bluekeep
- Pentest Tools List
- Hacker Security Tools
- Pentest Recon Tools
- Hacker Search Tools
- Hacking Tools For Pc
- Hacking Tools For Mac
- Hacker Hardware Tools
- Hacking Tools 2020
- Android Hack Tools Github
- Pentest Tools Nmap
- Hacker
- Pentest Tools Open Source
- Underground Hacker Sites
- Computer Hacker
- Nsa Hacker Tools
- Physical Pentest Tools
- Install Pentest Tools Ubuntu
- Hack Tools For Mac
- Hacking Tools Github
- Tools Used For Hacking
- Hack Tools
- Game Hacking
- Tools For Hacker
- Hackrf Tools
- Hacking Tools And Software
- Hacking Tools 2020
- Hacker Tools 2019
- Github Hacking Tools
- Hacking Tools For Games
- Github Hacking Tools
- What Is Hacking Tools
- Hacker Tools
- Termux Hacking Tools 2019
- Pentest Tools Website
- Pentest Tools Windows
- Tools Used For Hacking
- Pentest Tools Review
- Pentest Tools Windows
- Pentest Recon Tools
- Pentest Tools Framework
- Pentest Tools Nmap
- Pentest Tools For Ubuntu
- Pentest Tools Apk
- Hacker Tools Linux
- Hacking Tools For Games
- Easy Hack Tools
- Hacking Tools 2019
- New Hacker Tools
- Hacking Tools Github
- Android Hack Tools Github
- Hacking Apps
- Hack Tools Github
- Hacker Search Tools
- Hack Tool Apk
- Pentest Tools Review
- Pentest Tools Download
- Pentest Tools Website Vulnerability
- Hack App
- Hacking Tools Free Download
- Computer Hacker
- Hacker Security Tools
- Pentest Tools Alternative
- Hack Tools For Pc
- Pentest Box Tools Download
- Free Pentest Tools For Windows
- Hackrf Tools
- Hacker Tools For Windows
- Hacker Tools Hardware
- Hack Tools Download
- Hacking Tools For Beginners
- Tools Used For Hacking
- Nsa Hack Tools Download
- Pentest Tools Tcp Port Scanner






















